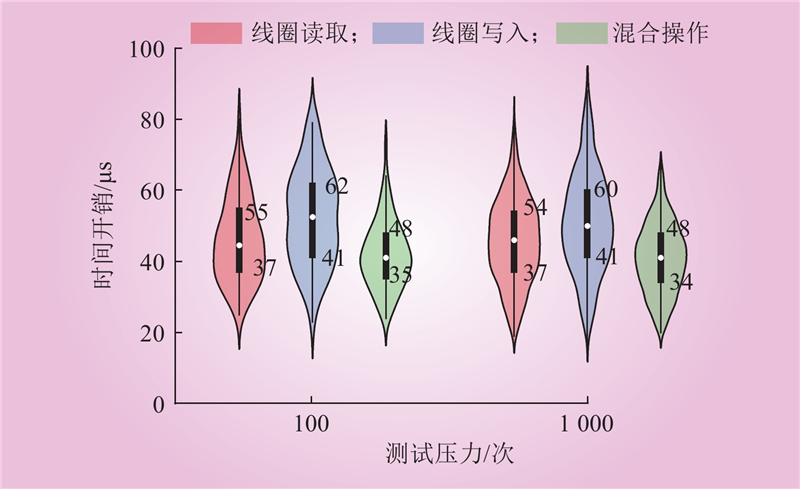
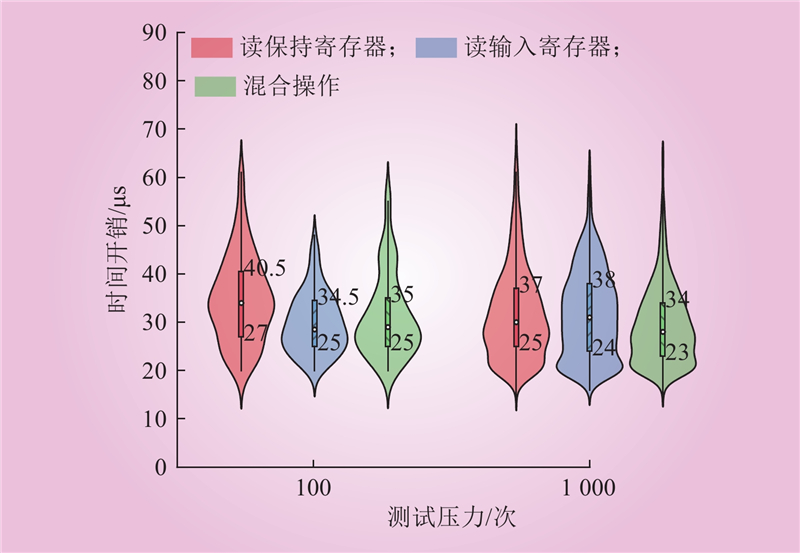
| 1 |
ORTIZ N, CARDENAS A A, WOOL A. A taxonomy of industrial control protocols and networks in the power grid[J]. IEEE Communications Magazine, 2023, 61 (6): 21- 27.
|
| 2 |
OCHIAI H, HOSSAIN M D, CHIRUPPHAPA P, et al. Modbus/RS-485 attack detection on communication signals with machine learning[J]. IEEE Communications Magazine, 2023, 61 (6): 43- 49.
|
| 3 |
SRIDHAR S, HAHN A, GOVINDARASU M. Cyber–physical system security for the electric power grid[J]. Proceedings of the IEEE, 2012, 100 (1): 210- 224.
|
| 4 |
SALODKAR P, NANDANWAR S, SAWARKAR S. Communication between energy meters and PLC based on modbus protocol[C]//2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT). Delhi, India. IEEE, 2023: 1–7.
|
| 5 |
MOHAMMED A S, SAXENA N, RANA O. Wheels on the modbus - attacking ModbusTCP communications[C]//Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks. San Antonio TX USA. ACM, 2022: 288–289.
|
| 6 |
杨国泰, 王宇飞, 罗剑波, 等. 电力CPS信息网络脆弱性及其评估方法[J]. 中国电力, 2018, 51 (1): 83- 89.
|
|
YANG Guotai, WANG Yufei, LUO Jianbo, et al. Electric CPS information network vulnerability and assessment method[J]. Electric Power, 2018, 51 (1): 83- 89.
|
| 7 |
HUITSING P, CHANDIA R, PAPA M, et al. Attack taxonomies for the Modbus protocols[J]. International Journal of Critical Infrastructure Protection, 2008, 1, 37- 44.
|
| 8 |
ZHANG Z Y, DENG R L, YAU D K Y, et al. Analysis of moving target defense against false data injection attacks on power grid[J]. IEEE Transactions on Information Forensics and Security, 2020, 15, 2320- 2335.
|
| 9 |
何金栋, 王宇, 赵志超, 等. 智能变电站嵌入式终端的网络攻击类型研究及验证[J]. 中国电力, 2020, 53 (1): 81- 91.
|
|
HE Jindong, WANG Yu, ZHAO Zhichao, et al. Type and verification of network attacks on embedded terminals of intelligent substation[J]. Electric Power, 2020, 53 (1): 81- 91.
|
| 10 |
ZHANG Z Y, DENG R L, YAU D K Y, et al. Zero-parameter-information data integrity attacks and countermeasures in IoT-based smart grid[J]. IEEE Internet of Things Journal, 2021, 8 (8): 6608- 6623.
|
| 11 |
DENG R L, XIAO G X, LU R X, et al. False data injection on state estimation in power systems—attacks, impacts, and defense: a survey[J]. IEEE Transactions on Industrial Informatics, 2017, 13 (2): 411- 423.
|
| 12 |
FOVINO I N, CARCANO A, MASERA M, et al. Design and implementation of a secure modbus protocol[M]//IFIP Advances in Information and Communication Technology. Berlin, Heidelberg: Springer Berlin Heidelberg, 2009: 83–96.
|
| 13 |
YI F M, ZHANG L, YANG S M, et al. A security-enhanced modbus TCP protocol and authorized access mechanism[C]//2021 IEEE Sixth International Conference on Data Science in Cyberspace (DSC). Shenzhen, China. IEEE, 2021: 61–67.
|
| 14 |
FERST M K, DE FIGUEIREDO H F M, DENARDIN G, et al. Implementation of secure communication with modbus and transport layer security protocols[C]//2018 13th IEEE International Conference on Industry Applications (INDUSCON). São Paulo, Brazil. IEEE, 2018: 155–162.
|
| 15 |
FIGUEROA-LORENZO S, AÑORGA J, ARRIZABALAGA S. A role-based access control model in modbus SCADA systems. A centralized model approach[J]. Sensors (Basel), 2019, 19 (20): E4455.
|
| 16 |
HUPP W, HASANDKA A, DE CARVALHO R S, et al. Module-OT: a hardware security module for operational technology[C]//2020 IEEE Texas Power and Energy Conference (TPEC). College Station, TX, USA. IEEE, 2020: 1–6.
|
| 17 |
LIN Y C, LIN C F, CHEN K H. Security enhancement of industrial Modbus message transmission with proxy approach[C]//2021 IEEE 3rd Eurasia Conference on IOT, Communication and Engineering (ECICE). Yunlin, Taiwan, China. IEEE, 2021: 90-95.
|
| 18 |
高魏轩. 基于Modbus协议的工业控制系统信息安全主动防御系统设计与实现[D]. 西安: 西安电子科技大学, 2018: 1–81.
|
|
GAO Weixuan. Design and implementation of industrial control system information security active defense system based on Modbus protocol[D]. Xi’an: Xidian University, 2018: 1–81.
|
| 19 |
KATULIC F, SUMINA D, ERCEG I, et al. Enhancing modbus/TCP-based industrial automation and control systems cybersecurity using a misuse-based intrusion detection system[C]//2022 International Symposium on Power Electronics, Electrical Drives, Automation and Motion (SPEEDAM). Sorrento, Italy. IEEE, 2022: 964–969.
|
| 20 |
王林浩, 吴桂初, 戴翀, 等. 智能断路器中Modbus/TCP协议的实时性能测试[J]. 中国电力, 2015, 48 (12): 6- 11.
|
|
WANG Linhao, WU Guichu, DAI Chong, et al. Research and testing of real-time performance of modbus/TCP protocol[J]. Electric Power, 2015, 48 (12): 6- 11.
|
| 21 |
席禹, 林冬, 于力, 等. 一种基于生物特征的电力系统安全认证协议[J]. 广东电力, 2022, 35 (10): 83- 90.
|
|
XI Yu, LIN Dong, YU Li, et al. Biometric based security authentication protocol for power system[J]. Guangdong Electric Power, 2022, 35 (10): 83- 90.
|
| 22 |
杨晋祥, 彭勇刚, 蔡田田, 等. 面向边缘计算的电力终端轻量级认证协议[J]. 中国电力, 2023, 56 (4): 88- 94.
|
|
YANG Jinxiang, PENG Yonggang, CAI Tiantian, et al. Power terminal lightweight authentication protocol for edge computing[J]. Electric Power, 2023, 56 (4): 88- 94.
|
| 23 |
程钎, 陈羽, 孙伶雁. 考虑服务配置的细粒度电力任务云边协同优化调度策略[J]. 电力系统保护与控制, 2023, 51 (7): 53- 62.
|
|
CHENG Qian, CHEN Yu, SUN Lingyan. Cloud-edge collaborative optimization scheduling strategy for fine-grained power tasks considering service configuration[J]. Power System Protection and Control, 2023, 51 (7): 53- 62.
|
| 24 |
彭鹏, 薛东. 基于边缘代理的云边协同物联网框架设计及其应用研究[J]. 广东电力, 2023, 36 (5): 18- 26.
|
|
PENG Peng, XUE Dong. Research on design of cloud side collaborative IOT framework based on edge agent and its application[J]. Guangdong Electric Power, 2023, 36 (5): 18- 26.
|
| 25 |
刘林彬, 苗泉强, 李俊娥. 基于模糊测试的GOOSE协议解析漏洞挖掘方法[J]. 中国电力, 2022, 55 (4): 33- 43.
|
|
LIU Linbin, MIAO Quanqiang, LI June. A method for mining GOOSE protocol parsing vulnerabilities based on fuzzing[J]. Electric Power, 2022, 55 (4): 33- 43.
|
| 26 |
The Modbus Organization. Modicon modbus protocol reference guide[EB/OL]. (1996-06)[2023-10-25]. https://modbus.org/docs/PI_MBUS_300.pdf.
|