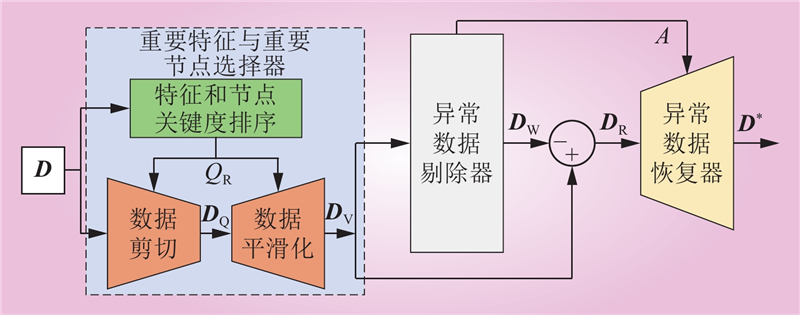
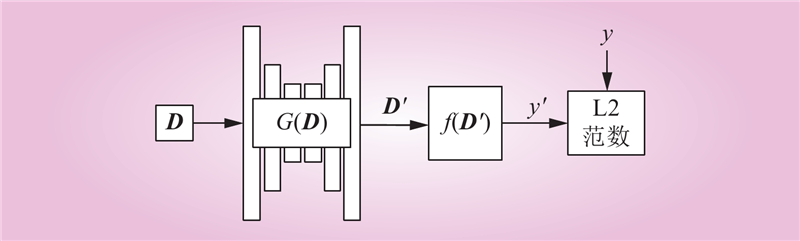
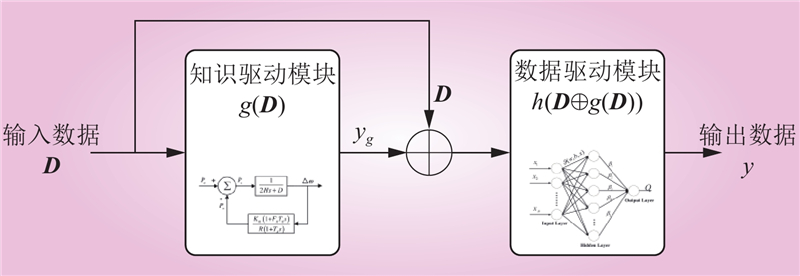
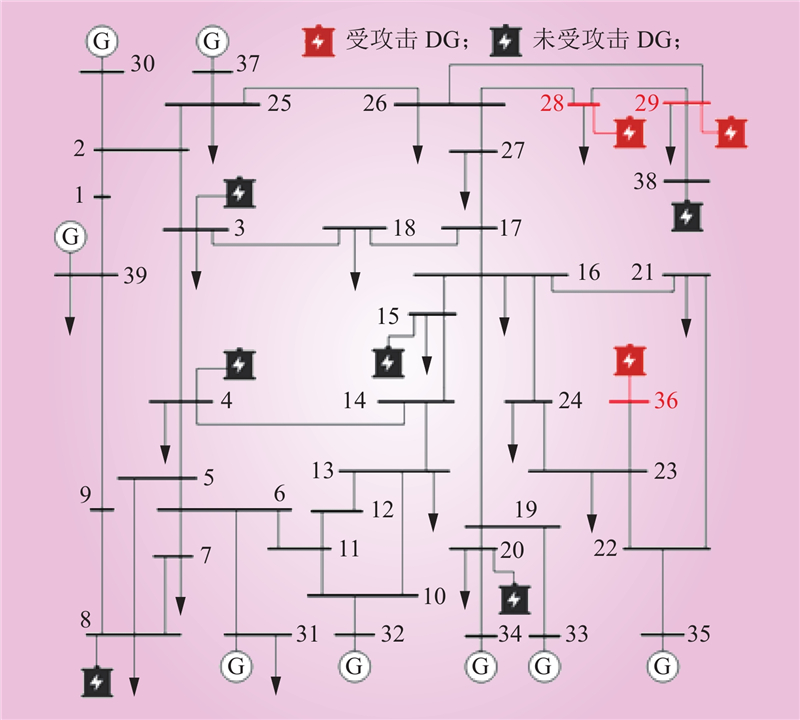
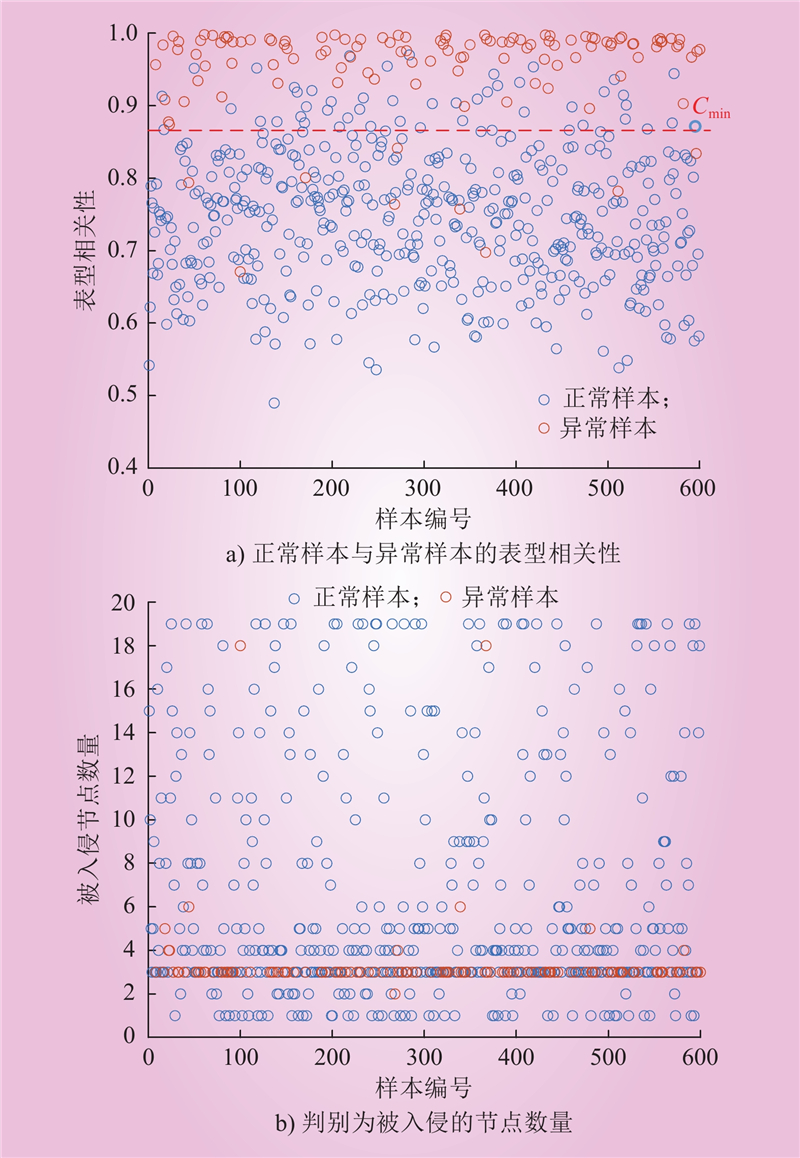
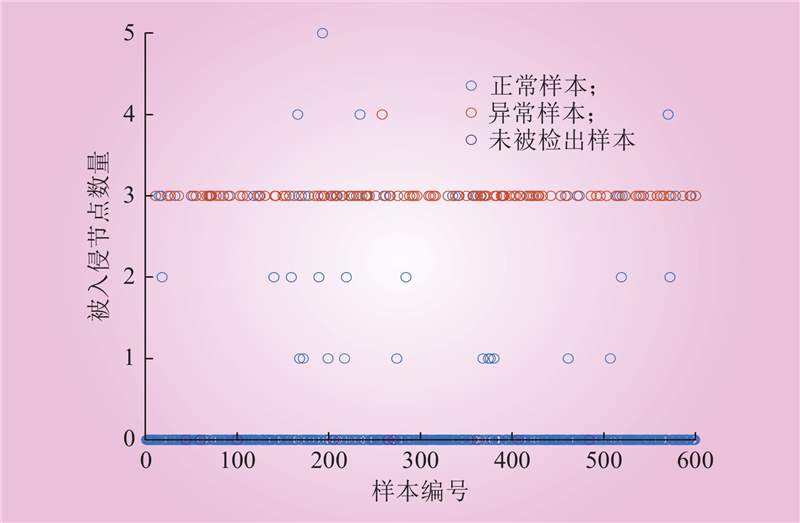
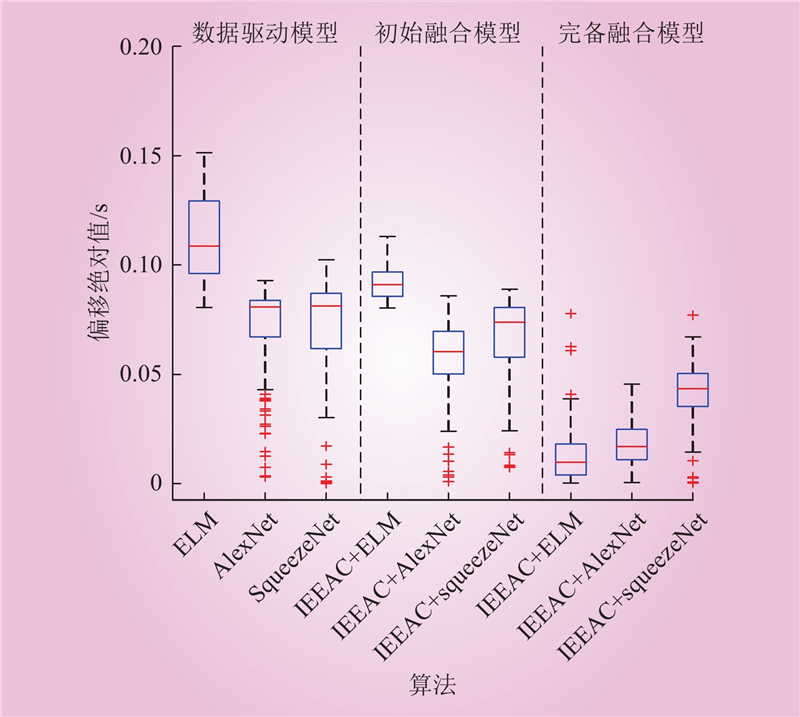
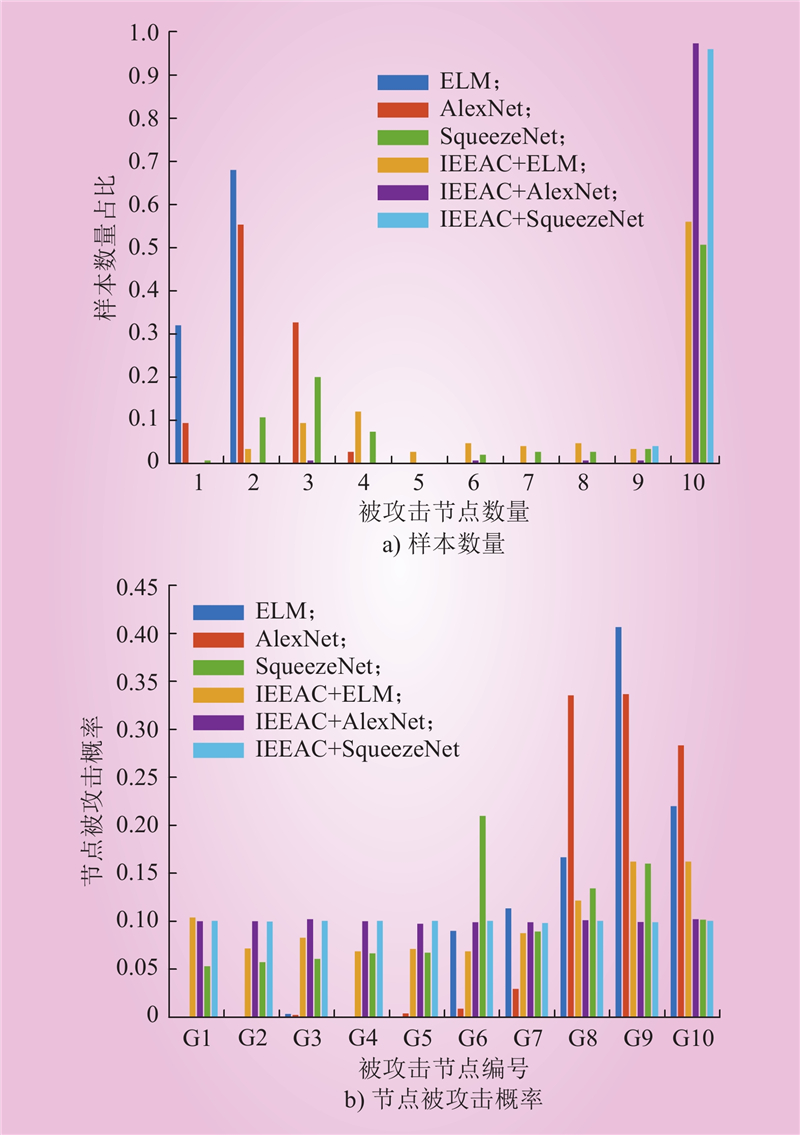
| 1 |
汤奕, 崔晗, 李峰, 等. 人工智能在电力系统暂态问题中的应用综述[J]. 中国电机工程学报, 2019, 39 (1): 2- 13, 315.
|
|
TANG Yi, CUI Han, LI Feng, et al. Review on artificial intelligence in power system transient stability analysis[J]. Proceedings of the CSEE, 2019, 39 (1): 2- 13, 315.
|
| 2 |
李峰, 王琦, 胡健雄, 等. 数据与知识联合驱动方法研究进展及其在电力系统中应用展望[J]. 中国电机工程学报, 2021, 41 (13): 4377- 4390.
|
|
LI Feng, WANG Qi, HU Jianxiong, et al. Combined data-driven and knowledge-driven methodology research advances and its applied prospect in power systems[J]. Proceedings of the CSEE, 2021, 41 (13): 4377- 4390.
|
| 3 |
黄书民, 蒋林高, 李志川, 等. 基于PSO寻优与DBN神经网络的电晕损耗预测[J]. 中国电力, 2022, 55 (6): 95- 102, 214.
|
|
HUANG Shumin, JIANG Lingao, LI Zhichuan, et al. Corona loss prediction of UHV AC transmission line based on DBN neural network optimized by PSO[J]. Electric Power, 2022, 55 (6): 95- 102, 214.
|
| 4 |
李丰君, 王磊, 赵健, 等. 基于天气融合和LSTM网络的分布式光伏短期功率预测方法[J]. 中国电力, 2022, 55 (11): 149- 154.
|
|
LI Fengjun, WANG Lei, ZHAO Jian, et al. Research on distributed photovoltaic short-term power prediction method based on weather fusion and LSTM-net[J]. Electric Power, 2022, 55 (11): 149- 154.
|
| 5 |
杨胡萍, 余阳, 汪超, 等. 基于VMD-CNN-BIGRU的电力系统短期负荷预测[J]. 中国电力, 2022, 55 (10): 71- 76.
|
|
YANG Huping, YU Yang, WANG Chao, et al. Short-term load forecasting of power system based on VMD-CNN-BIGRU[J]. Electric Power, 2022, 55 (10): 71- 76.
|
| 6 |
杨朋朋, 王蓓蓓, 胥鹏, 等. 不完全信息下基于深度双Q网络的发电商三段式竞价策略[J]. 中国电力, 2021, 54 (11): 47- 58.
|
|
YANG Pengpeng, WANG Beibei, XU Peng, et al. Three-stage bidding strategy of generation company based on double deep Q-network under incomplete information condition[J]. Electric Power, 2021, 54 (11): 47- 58.
|
| 7 |
YU J J Q, HOU Y H, LI V O K. Online false data injection attack detection with wavelet transform and deep neural networks[J]. IEEE Transactions on Industrial Informatics, 2018, 14 (7): 3271- 3280.
|
| 8 |
王健, 易姝慧, 刘俊杰, 等. 基于随机森林算法和稳态波形的非介入式工业负荷辨识[J]. 中国电力, 2022, 55 (2): 82- 89.
|
|
WANG Jian, YI Shuhui, LIU Junjie, et al. Non-intrusive industrial load identification based on random forest algorithm and steady-state waveform[J]. Electric Power, 2022, 55 (2): 82- 89.
|
| 9 |
严宇, 刘天琪. 基于决策表-粗糙集理论的动态安全分析神经网络输入特征优选[J]. 电力系统自动化, 2004, 28 (15): 25- 29.
|
|
YAN Yu, LIU Tianqi. Ann injection features optimization of dynamic security analysis based on decision tables-rough set theory[J]. Automation of Electric Power Systems, 2004, 28 (15): 25- 29.
|
| 10 |
ZHANG Y, KRISHNAN V V G, PI J, et al. Cyber physical security analytics for transactive energy systems[J]. IEEE Transactions on Smart Grid, 2020, 11 (2): 931- 941.
|
| 11 |
QU Y Y, POKHREL S R, GARG S, et al. A blockchained federated learning framework for cognitive computing in industry 4.0 networks[J]. IEEE Transactions on Industrial Informatics, 2021, 17 (4): 2964- 2973.
|
| 12 |
GOLDBLUM M, TSIPRAS D, XIE C, et al. Dataset security for machine learning: data poisoning, backdoor attacks, and defenses[J]. IEEE Trans Pattern Anal Mach Intell, 2023, 45 (2): 1563- 1580.
|
| 13 |
NIAZAZARI I, LIVANI H. Attack on grid event cause analysis: an adversarial machine learning approach[C]//2020 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT). Washington, DC, USA. IEEE, 2020: 1–5.
|
| 14 |
REN C, DU X N, XU Y, et al. Vulnerability analysis, robustness verification, and mitigation strategy for machine learning-based power system stability assessment model under adversarial examples[J]. IEEE Transactions on Smart Grid, 2022, 13 (2): 1622- 1632.
|
| 15 |
PAUL S, NI Z, MU C X. A learning-based solution for an adversarial repeated game in cyber–physical power systems[J]. IEEE Transactions on Neural Networks and Learning Systems, 2020, 31 (11): 4512- 4523.
|
| 16 |
TIAN J W, WANG B H, WANG Z, et al. Joint adversarial example and false data injection attacks for state estimation in power systems[J]. IEEE Transactions on Cybernetics, 2022, 52 (12): 13699- 13713.
|
| 17 |
SU J W, VARGAS D V, SAKURAI K. One pixel attack for fooling deep neural networks[J]. IEEE Transactions on Evolutionary Computation, 2019, 23 (5): 828- 841.
|
| 18 |
GOSWAMI G, AGARWAL A, RATHA N, et al. Detecting and mitigating adversarial perturbations for robust face recognition[J]. International Journal of Computer Vision, 2019, 127 (6/7): 719- 742.
|
| 19 |
JIN G Q, SHEN S W, ZHANG D M, et al. APE-GAN: adversarial perturbation elimination with GAN[C]//2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). Brighton, United Kingdom. IEEE, 2019: 3842–3846.
|
| 20 |
LIAO F Z, LIANG M, DONG Y P, et al. Defense against adversarial attacks using high-level representation guided denoiser[C]//2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition. Salt Lake City, UT. IEEE, 2018: 1778–1787.
|
| 21 |
CHIANG P Y, GEIPING J, GOIDBUIM M, et al. Witchcraft: Efficient PGD attacks with random step size[C]//2020 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). Barcelona, Spain. IEEE, 2020: 3747–3751.
|
| 22 |
WENG J, LUO Z, LI S, et al. Logit margin matters: Improving transferable targeted adversarial attack by logit calibration[J]. IEEE Transactions on Information Forensics and Security, 2023, 18, 3561- 3574.
|
| 23 |
HEO B, LEE M, YUN S, et al. Knowledge distillation with adversarial samples supporting decision boundary[J]. Proceedings of the AAAI Conference on Artificial Intelligence, 2019, 33 (1): 3771- 3778.
|
| 24 |
TIAN J W, LI T Y, SHANG F T, et al. Adaptive normalized attacks for learning adversarial attacks and defenses in power systems[C]//2019 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm). Beijing, China. IEEE, 2019: 1–6.
|
| 25 |
TIAN J W, WANG B H, LI J, et al. Adversarial attacks and defense for CNN based power quality recognition in smart grid[J]. IEEE Transactions on Network Science and Engineering, 2022, 9 (2): 807- 819.
|
| 26 |
REN C, XU Y. A universal defense strategy for data-driven power system stability assessment models under adversarial examples[J]. IEEE Internet of Things Journal, 2023, 10 (9): 7568- 7576.
|
| 27 |
HUANG R, LI Y C. Adversarial attack mitigation strategy for machine learning-based network attack detection model in power system[J]. IEEE Transactions on Smart Grid, 2023, 14 (3): 2367- 2376.
|
| 28 |
黄冬梅, 丁仲辉, 胡安铎, 等. 低成本对抗性隐蔽虚假数据注入攻击及其检测方法[J]. 电网技术, 2023, 47 (4): 1531- 1540.
|
|
HUANG Dongmei, DING Zhonghui, HU Anduo, et al. Low-cost adversarial stealthy false data injection attack and detection method[J]. Power System Technology, 2023, 47 (4): 1531- 1540.
|
| 29 |
ATHAY T, PODMORE R, VIRMANI S. A practical method for the direct analysis of transient stability[J]. IEEE Transactions on Power Apparatus Systems, 1979, 98 (2): 573- 584.
|
| 30 |
LI F, WANG Q, TANG Y, et al. An integrated method for critical clearing time prediction based on a model-driven and ensemble cost-sensitive data-driven scheme[J]. International Journal of Electrical Power & Energy Systems, 2021, 125, 106513.
|